A technique for encrypting, protecting, and authenticating internet interactions is called Secure Sockets Layer, or SSL for short. The name “SSL” is still often used to refer to the older SSL protocol even though Transport Layer Security (TLS) is a far more contemporary and better technology.
Although email, VoIP, and other types of communication sent over unprotected networks may also be protected, SSL and TLS are most often used to safeguard interactions between a client and a server. As you can have a proper idea about https vs ssl you can have a fair understanding for the same.
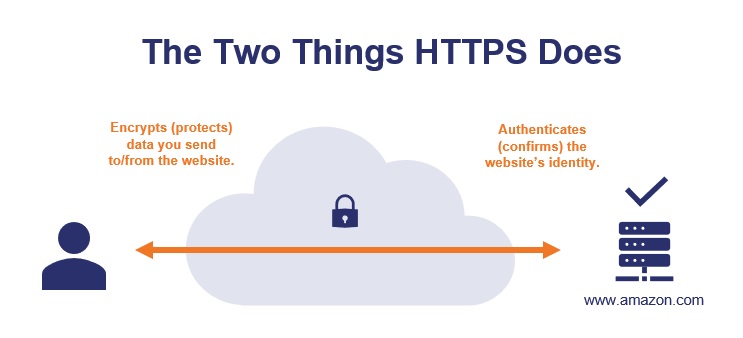
Comparing https vs ssl, it’s evident that HTTPS, which stands for Hypertext Transfer Protocol Secure, is a more advanced and secure protocol compared to SSL, or Secure Sockets Layer, as it not only encrypts the data transmitted between a user’s browser and the server but also authenticates the website, ensuring a safer online browsing experience.
The following fundamental ideas must be understood in order to comprehend SSL and TLS
A TLS handshake is the initial step in establishing a secure connection between two parties. At this point, a secure connection is formed, and parties trade public keys.
- The communicating parties create session keys during the TLS handshake, which are used to encrypt and decode any further communications between them.
- New session keys are created at the beginning of each session and used to encrypt the supplied data.
- A user may use TLS to verify that the website they are communicating with is who they say it is. In this way, the user’s privacy will be protected.
- To further guarantee that the data hasn’t been tampered with, all transfers also include a message authentication code (MAC), as provided by Transport Layer Security (TLS).
TLS encrypts both the data that visitors provide to websites through clicks and form submissions as well as the data that websites give back to those same visitors via HTTP answers. The receiver must use a unique key to unlock every encrypted data.
The use of a handshake in TLS
The TLS handshake starts each and every TLS-based communication session. During a TLS handshake, an asymmetric encryption technique is used. Each party participating in this kind of encryption must use their own distinct keys in order for it to function. This is a reality thanks to the discipline of public-key cryptography.
Two keys are used in public key cryptography
A public key that is made public and a private key that is kept private and used only by the server. Only the appropriate private key may be used to decode data that has been encrypted using the public key.
The client and server will exchange data generated at random using their respective public and private keys during the handshake phase of the TLS protocol. This data will be used to produce session keys, which are needed for encryption.
Conclusion
In contrast to asymmetric encryption, symmetric encryption demands that both parties to a communication have access to the same key in order to decode the data. The same session keys will be used to encrypt data on both ends after the conclusion of the TLS handshake. The initial public and private keys are no longer required when using session keys. After a session is over, temporary “session keys” are discarded and never utilised again. For the subsequent session, fresh, completely random session keys will be generated.




